One of the critical things we get asked when working with our customers is "how do we know if we have enough security on our website", or thereabouts.
We believe that the real question they are asking is "Are we likely to get hacked/breached and what are we doing to prevent it?". With ransomware attacks, Denial of Service (DDoS) and general cyberattacks happening almost weekly (check out the growing list on Wikipedia), it really is a priority topic for many organisations. In this latest post on Sitecore Security, we have listed several of our top solutions for protecting your Sitecore (and other enterprise Martech) applications;
SSL, or SSL?
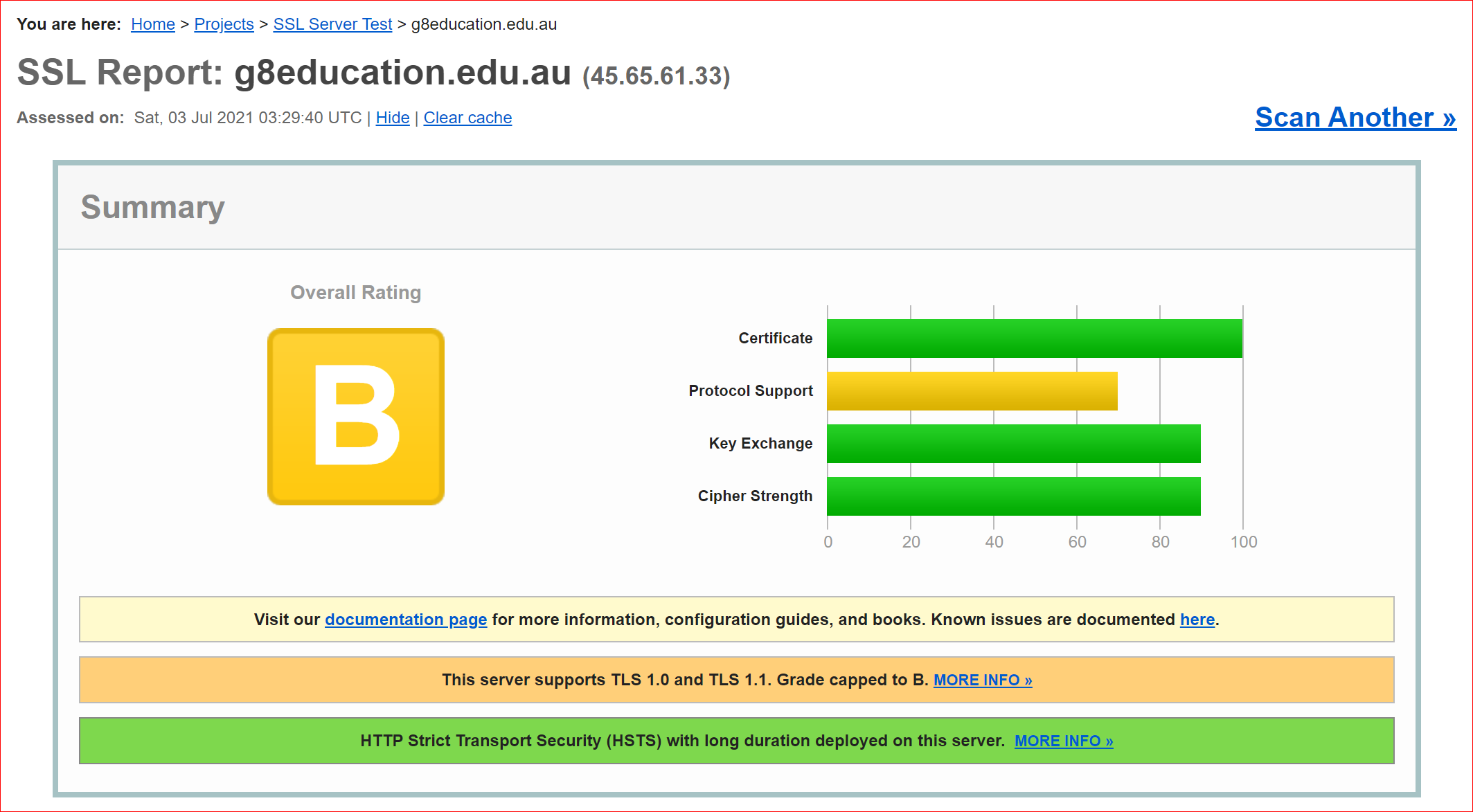
In this article by Globalsign they talk about the different types of certificates available to organisations. Whilst the "Green Validation Bar" of IE11 days is somewhat gone, the stronger a certificate is validated the better it will perform for your organisation. It also comes down to how your Certificate is installed, the encryption model you are using and deeper things like Ciphers; you can test your certificate using https://www.ssllabs.com/ssltest/ if you aren't getting an A+ core, talk to your web team today.
Azure Security Center
When deploying assets in the Microsoft Azure Cloud there are a range of best practices that should be adhered too and with the constantly evolving landscape of new assets, compliance changes and inevitably, people changes within your teams, Azure Security Center provides a comprehensive overview of your organisations Security Posture. Enable it today within your Tenancy/Subscription and understand your Secure Score, working through each recommendation to achieve a Secure Score that meets your organisational security baseline.
Whilst there is some overlap with Azure Security Center, the two work hand in hand. Azure Sentinel is a security information event management (SIEM) tool that focuses on analysing the data supplied to it from your Azure (and non-Azure) based services, such as server logs, network logs, firewall logs. It will detect events within your data in real time, match them against common known threats and provide the security orchestration you need to mitigate threats.
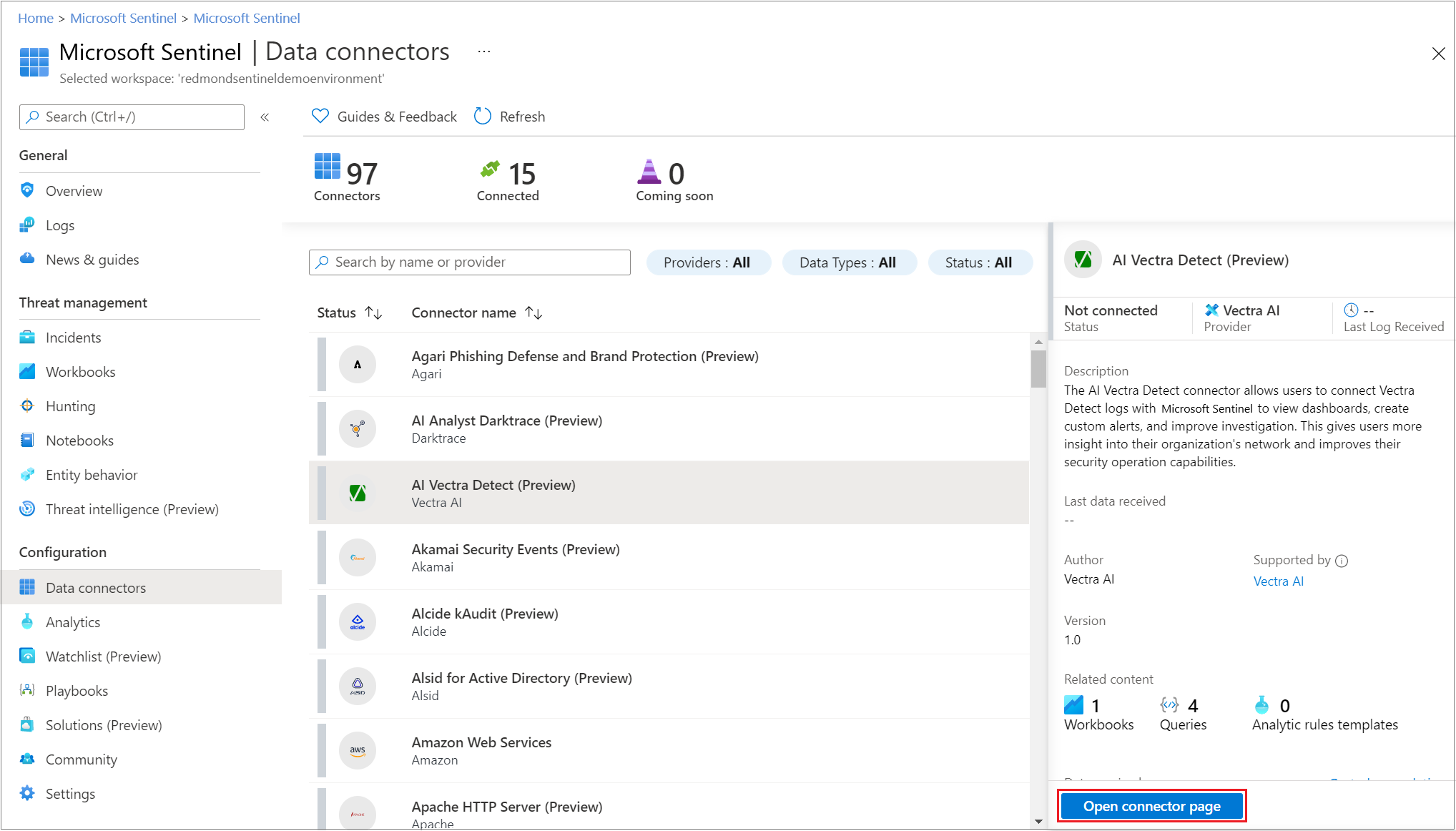
In the simplest of use cases, it can provide you alerts to you team when a threat is happening, in perhaps more advanced use cases you can connect to Azure Automation and run scripts that scale, hide, move, obfuscate or lockdown your Cloud resources. In combination with Azure Front Door (with WAF enabled) we believe Sentinel provides the real-time intelligence we need to mitigate common threats such as the OWASP Top 10.
Networking Restrictions
Assuming you are deploying Sitecore correctly in a Scaled configuration, its important to restrict the App Services so only trusted actors can access them. With multiple approaches to securing Web Apps and SQL, you must implement at minimum, Azure IP restrictions. By securing all Sitecore Web App roles (excluding Content Delivery servers of course), you are adding that first and most important layer of protection.
With further evolution you may choose to automate how you apply IP Restrictions through your Infrastructure deployment pipelines. Don't forget to be diligent with IP Restrictions and refrain from allowing public non-static IP addresses from home based users. We use OpenVPN Cloud to managed controlled access to client environments, in combination with approved client corporate network IPs to control access.
Role Based Access Control (RBAC)
RBAC is a critical part of security, we believe in a Principle of Least Privilege (PoLP) model. By reducing exposure to the Azure Portal (in some cases to zero-access, if you have the right DevOps and tooling in place, and should you require access to be provided to the Production resources, deliver access through Office 365, Azure AD Joined accounts that map to a clear RBAC Policy. Azure AD provides a number of pre-defined roles you can pick from, or alternatively you can create custom roles to define how your people and different people within the team can perform tasks on Azure.
RBAC when working within Microsoft Azure and Azure DevOps is powerful as its a share access and login mechanism, meaning you can control access to both tools using a common login through Azure Active Directory. Whilst this sounds obvious, when working with 3rd party tools outside of the Microsoft Ecosystem, Single Sign On is an often overlooked configuration and maintenance overhead (just checkout how complex the Octopus Deploy documentation is, and they are good at this!). Don't get us wrong, we love Octopus Deploy, but be mindful of the cost vs. security when securing your environment.
Privileged Identity Management (PIM)
Not a fundamental, but worth mentioning for organisations with strict requirements, we recommend PIM. PIM allows you to provide as-needed and just-in-time access to Azure resources and Azure DevOps. The concept of PIM is being able to demonstrate that access to resources in Azure is permitted, but it needs to be audited and approved. The only down side of PIM is that it requires Premium Azure AD and Office 365 accounts. Read more about Privileged Identity Management on the Microsoft website.
In summary, security is an ongoing focus for organisations and whilst these Sitecore Azure security fundamentals are just that, fundamentals, they need ongoing optimisations and focus. Think about how your organisation can revisit these tools and processes and use them to protect against and mitigate threats.
To find out more visit https://www.dataweavers.com/cio/cybersecurity
For more resources visit https://www.dataweavers.com/cio/security





